Packets transmitted between neighbors must be validated to ensure that only devices with the same preshared authentication key accept packets. Authentication for the EIGRP is a customizable per interface, which implies that packets sent between neighbors connected by an interface are authenticated.
To prevent the introduction of unwanted information from unapproved sources, EIGRP offers message-digest algorithm 5 (MD5) authentication. RFC 1321 defines MD5 authentication.
In this post, I will explain how to set up name mode authentication.
What is EIGRP SHA Authentication and how does it work?
The Hashed Message Authentication Code-Secure Hash Algorithm-256 (HMAC-SHA-256) authentication technique is also supported by EIGRP. A shared secret key is configured on all devices connected to a common network when you use the HMAC-SHA-256 authentication method.
The key is used to produce and verify a message digest, which is then added to each packet. The packet's and secret key's message digest is a one-way function. EIGRP packets will be authenticated using HMAC-SHA-256 message authentication codes if HMAC-SHA-256 authentication is configured in an EIGRP network.
The HMAC method takes the data to be authenticated (the EIGRP packet) as input and outputs a 256-bit hash that is utilized for authentication. The packet is accepted by the recipient if the hash value provided by the sender matches the hash value determined by the receiver; otherwise, the packet is rejected.
Since IOS 15, EIGRP includes a new configuration mechanism known as named mode EIGRP. We configured EIGRP globally and certain other things (like authentication) on the interfaces with the "old" version of EIGRP that we used before IOS 15. Everything is done globally with the named mode EIGRP.
Further, you will learn how to configure authentication using the "EIGRP Name mode" configuration.
EIGRP used to only accept MD5 authentication, however from IOS 15.1(2)S and 15.2(1)T, we can also utilize SHA-256. This method of authentication is now significantly more secure than MD5. MD5 authentication can be set up in either named or classic form, however, SHA authentication can only be set up in named mode.
When configuring SHA authentication, you can specify whether you want to utilize merely an interface password or a key chain as well. The advantage of utilizing merely a password is that it's easier to set up. The negative is that if you want to change the password on one of your routers, your neighbor adjacency will drop.
When using a key chain, rotating keys are available, allowing us to change passwords without losing the neighbor adjacency.
Also Read:
The benefit of Using EIGRP named Mode Authentication:
This option allows you to employ Secure Hash Algorithms with an h-based Message Authentication Code (HMAC). Algorithms with SHA2-256 bits EIGRP packets now include SHA2-256 HMAC authentication, which ensures that users' routers only receive routing updates from other routers who have the same pre-shared key.
This prevents someone from adding another router to the network on purpose or by accident, producing a problem.
The SHA2 key is made up of the user-configured shared secret key and the IPv4/IPv6 address from where the packet is being sent. "Hello" Packet DoS replay attacks with a faked source address are no longer possible.
Using a common 'password,' a simpler configuration mode is available. When further security is required, keychain support is available.
In Classic Mode, EIGRP provides MD5 authentication, while in Multi-AF (Named) Mode, EIGRP supports both MD5 and SHA-256 authentication. The key chain is defined globally for MD5 authentication in both Classic and Named modes.
The key chain can have many keys, however, in EIGRP packets, only the lowest active key number is shared.
Because this number is shared in the hello packets, the key ID must match for authentication to take place. Authentication is applied at the link level in Classic Mode, whereas it is applied at the AF-interface mode in Named Mode.
EIGRP authentication was previously configured in interface mode and only supported Message Digest 5 (MD5) authentication, as illustrated below:
R2(config)#interface f0/1
R2(config-if)#ip authentication mode eigrp 10 md5
R2(config-if)# ip authentication key-chain eigrp 10 EIGRPKEY
Authentication can be configured in two ways in the "EIGRP NAME" configuration:
- Only one password is required for configuration.
- Key-chains can be used to enhance extra security.
Although hmac-sha-256 authentication can be configured directly on the interface, it is not feasible to set the time and duration for which the authentication will be valid in this mode.
The shared secret key is usually set to be the same for both the sender and the receiver. The shared secret key for a packet is defined as the concatenation of the user-configured shared secret (identical across all devices participating in the authenticated domain) and the IPv4 or IPv6 address (which is unique for each device) from which the packet is sent to protect against packet replay attacks due to a spoofed source address.
The hash to be sent is calculated by the device transmitting the packet using the following formula:
- The configured shared secret is the first component of the key.
- The local interface address from which the packet will be sent is the second key part.
- Data is the EIGRP packet that will be sent (prior to the addition of the IP header).
The hash for verification is calculated by the device receiving the packet using the following formula:
- The configured shared secret is the first component of the key.
- The IPv4 or IPv6 source address in the IPv4 or IPv6 packet header is the second most important section.
- Data—the received EIGRP packet (after removing the IP header).
All of the following must be true for effective authentication:
- Both the sender and the recipient must know the same shared secret.
- The sender's source address must match the source address in the IP header received by the receiver.
- The data in the EIGRP packets that the sender sends must match the data in the EIGRP packets that the receiver receives.
If any of the following is true, authentication will fail:
- The sender is unaware of the receiver's intended shared secret.
- In transit, the IP source address in the IP header is changed.
- Any EIGRP packet data is altered while in transit.
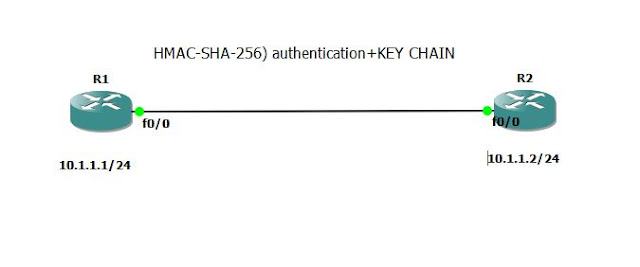
HMAC-SHA-256) Authentication + KEY CHAIN Configuration
SHA -Secure Hash Algorithms
R1 Configuration:
R1#conf t
R1(config)#interface f0/0
R1(config-if)#ip address 10.1.1.1 255.255.255.0
R1(config-if)#no shut
R1(config)#router eigrp MY
R1(config-router)#address-family ipv4 unicast autonomous-system 10
R1(config-router-af)#network 10.1.1.0 0.0.0.255
R1(config-router-af)#af-interface f0/0
R1(config-router-af-interface)#authentication mode hmac-sha-256 SECRET_KEY
To Verify:
R1#sh eigrp address-family ipv4 interfaces detail f0/0
EIGRP-IPv4 VR(MY) Address-Family Interfaces for AS(10)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Fa0/0 0 0/0 0/0 0 0/0 0 0
Hello-interval is 5, Hold-time is 15
Split-horizon is enabled
Next xmit serial <none>
Packetized sent/expedited: 0/0
Hello's sent/expedited: 54/1
Un/reliable mcasts: 0/0 Un/reliable ucasts: 0/0
Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0
Retransmissions sent: 0 Out-of-sequence rcvd: 0
Topology-ids on interface - 0
Authentication mode is HMAC-SHA-256, key-chain is not set
Before Authentication:
R1#debug eigrp packets
(UPDATE, REQUEST, QUERY, REPLY, HELLO, UNKNOWN, PROBE, ACK, STUB, SIAQUERY, SIAREPLY)
EIGRP Packet debugging is on
R1#
*Mar 28 12:13:22.663: EIGRP: Fa0/0: ignored packet from 10.1.1.2, opcode = 5 (missing authentication or key-chain missing)
After Authentication
R1#debug eigrp packets
(UPDATE, REQUEST, QUERY, REPLY, HELLO, UNKNOWN, PROBE, ACK, STUB, SIAQUERY, SIAREPLY)
EIGRP Packet debugging is on
R1#
*Mar 28 12:15:49.131: EIGRP: Sending TIDLIST on FastEthernet0/0 - 1 items
*Mar 28 12:15:49.135: EIGRP: Sending HELLO on Fa0/0 - paklen 86
*Mar 28 12:15:49.135: AS 10, Flags 0x0:(NULL), Seq 0/0 interfaceQ 0/0 iidbQ un/rely 0/0
*Mar 28 12:15:49.167: EIGRP: received packet with HMAC-SHA-256 authentication
*Mar 28 12:15:49.167: EIGRP: Received HELLO on Fa0/0 - paklen 86 nbr 10.1.1.2
*Mar 28 12:15:49.171: AS 10, Flags 0x0:(NULL), Seq 0/0 interfaceQ 0/0 iidbQ un/rely 0/0 peerQ
R1#sh ip eigrp neighbors
EIGRP-IPv4 VR(MY) Address-Family Neighbors for AS(10)
H Address Interface Hold Uptime SRTT RTO Q Seq
(sec) (ms) Cnt Num
0 10.1.1.2 Fa0/0 11 00:16:54 144 864 0 4
R1#conf t
R1(config)#key chain MYCHAIN
R1(config-keychain)#key 1
R1(config-keychain-key)#key-string CISCO
R1(config-keychain-key)#exit
R1(config)#router eigrp MY
R1(config-router)#ADdress-family ipv4 unicast autonomous-system 10
R1(config-router-af)#af-interface f0/0
R1(config-router-af-interface)#authentication key-chain MYCHAIN
Verify:
R1#sh ip eigrp interfaces detail
EIGRP-IPv4 VR(MY) Address-Family Interfaces for AS(10)
Xmit Queue PeerQ Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable Un/Reliable SRTT Un/Reliable Flow Timer Routes
Fa0/0 1 0/0 0/0 144 0/1 50 0
Hello-interval is 5, Hold-time is 15
Split-horizon is enabled
Next xmit serial <none>
Packetized sent/expedited: 2/0
Hello's sent/expedited: 351/3
Un/reliable mcasts: 0/2 Un/reliable ucasts: 3/5
Mcast exceptions: 0 CR packets: 0 ACKs suppressed: 0
Retransmissions sent: 3 Out-of-sequence rcvd: 1
Topology-ids on interface - 0
Authentication mode is HMAC-SHA-256, key-chain is "MYCHAIN"
R2 Configuration
R2(config)#interface f0/0
R2(config-if)#ip address 10.1.1.2 255.255.255.0
R2(config-if)#no shut
R2(config-if)#exit
R2(config)#router eigrp MY
R2(config-router)#address-family ipv4 unicast autonomous-system 10
R2(config-router-af)#network 10.1.1.0 0.0.0.255
R2(config-router-af)#af-interface f0/0
R2(config-router-af-interface)#authentication mode hmac-sha-256 SECRET_KEY
R2(config)#key chain MYCHAIN
R2(config-keychain)#key 1
R2(config-keychain-key)#key-string CISCO
R2(config-keychain-key)#exit
R2(config)#router eigrp MY
R2(config-router)#address-family ipv4 unicast autonomous-system 10
R2(config-router-af)#af-interface f0/0
R2(config-router-af-interface)#authentication key-chain MYCHAIN
FAQs: EIGRP HMAC-SHA-256 Authentication
Q: Is authentication enabled for routing protocols?
Ans: Most routing protocols implement authentication in one of two ways: utilizing a routing protocol-centric solution that configures the passwords or keys to use within the routing protocol configuration, or using a broader solution that uses separately specified keys.
Q: Is EIGRP safe?
Ans: MD5 is supported by EIGRP authentication. When this option is enabled, routers authenticate the source of each routing update packet they receive. The setup below prevents an intruder from establishing a bogus EIGRP adjacency. The result of bogus adjacency can be CPU overutilization or routing table poisoning.
Q: Is load balancing supported by EIGRP?
Ans: EIGRP, like OSPF or RIP, can perform load balancing, but it has one more trick up its sleeve. Both RIP and OSPF can perform load balancing, but the paths must be equal.
Q: What exactly is an EIGRP stub?
Ans: Stub routers in EIGRP are nodes that are only directly connected to networks and are not intended to be in data plane transit. EIGRP stub routers are intended for very small branch office routers or network edges.
Q: How do I protect my routing?
Ans: We may protect routing protocols such as RIP, EIGRP, and OSPF by adding authentication to them by constructing a key chain and applying it to the interface on which the routes are advertised. Instead of discussing protocols, we will focus on RIP, EIGRP, and OSPF authentication.
Q: What exactly is routing security?
Ans: Router security, on the other hand, entails hardening or securing the routers in order to safeguard the network as a whole. It specifically covers stopping attackers from Using routers to gather network information for use in an attack (information leakage) and Turning off your routers (and therefore your network).
Q: What is the distinction between routing protocols and routed protocols?
Ans: A Routing Protocol learns routes (paths) for a Routed Protocol, and Routed Protocols include IP (Internet Protocol), IPX (Internetwork Packet Exchange), and Appletalk.
Conclusion
Since IOS 15.1(2)S and 15.2(1)T, EIGRP has supported SHA authentication. If at all possible, utilize SHA authentication instead of MD5. MD5 authentication can be set up in either a traditional or a named manner.
The only named mode supports SHA-256 Authentication. You have the option of using a single password or including a key chain. The key chain has the advantage of allowing you to change passwords without having to reset the neighbor adjacency.
Explore More:


![The Best Antivirus Apps For Android - [2023] The Best Antivirus Apps For Android - [2023]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj3Yjm36h1U18dmYifXs9XZCUy6ch_XK0XOXf8hVW4zcVUDW0OiVXQZT0Sr77Yjep1CUOHP3OqlrMIzRJLYasizRmQUilnXjozbQ8D0iroUBbeFEUD2MwaJdGuE4RJaqrfVHFX-_OoIhOyPr_K10ky6goZUJtdqUWIOkCibIoNylnXXzR-AksQYPTQ0/s72-w640-c-h388/antivirus-android-2023.png)
![15 Travel Packing Tips For Holiday: Updated [2023] 15 Travel Packing Tips For Holiday: Updated [2023]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgJfOBYMtma5U34TjVvkOWNnaRwVA_ty2-tKck6tTU24-cAcOu4boybt3T_8BF66hAqzOriHVxJdRbzjLq9ZfhsMAUTQ80ja19GPktAAEnW0WPKQgsKJTXXJzIeKHYE40HeljCSC6UVTJA/s72-w640-c-h360/Travel-packing.jpg)


0 Comments: