Generic Routing Encapsulation (GRE) Overview
Why is a GRE tunnel required?
How does GRE tunnel work?
Advantages of Generic Routing Encapsulation
The GRE protocol has several advantages, including:
- Multiple protocols are used over a single protocol backbone.
- Providing workarounds for networks with a small number of hops
- Non-contiguous subnetworks are linked together.
- Being less resource-intensive than its competitors (e.g. IPsec VPN)
- GRE tunnels encapsulate multiple protocols on a single protocol backbone.
- GRE tunnels are useful for networks with a limited number of hops.
- GRE tunnels connect disparate subnetworks.
- GRE tunnels enable VPNs to be established across WANs.
Generic Routing Encapsulation(GRE) vs IPsec
Configuring GRE Tunneling
To get started, you'll need two pieces of information.
Your IP address is what GRE tunnels rely on. This is not the same as a human-friendly URL. An IP address consists of numbers and decimals.
The IP address of your recipient. You'll need the same information for the node to which you want to connect.
There are five steps you can apply in configuring a GRE tunnel:
Step 1: Use the interface tunnel number global configuration command to create a tunnel interface.
Step 2: Use the IP address IP-address interface configuration command to assign an IP address to the tunnel interface. Normally, this is a private IP address.
Step 3: Use the tunnel source IP-address | interface-name interface configuration command to specify the tunnel source IP address or source interface.
Step 4: Use the tunnel destination IP-address interface configuration command to specify the tunnel destination IP address.
Step 5. (Optional) To specify GRE tunnel mode, use the "tunnel mode GRE IP" command.
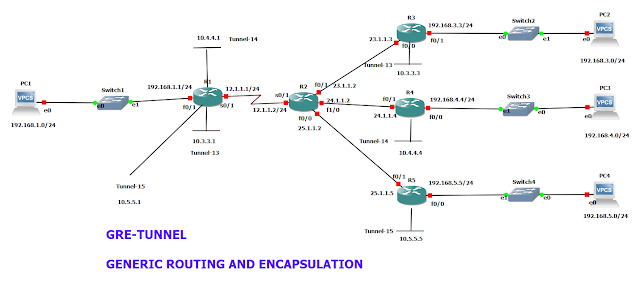
The sample configuration in the following example depicts a basic GRE tunnel between R1 and R3, R1 and R4, R1 and R5, and R1 and R6.
Configurations are step by step.
R1(config)#int f0/1
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#ip add 12.1.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#
For the physical interface and the tunnel interface, use the show IP interface brief command on all routers to ensure that the tunnel interfaces are operational and configured with the correct IP addresses.
R1#sh ip int br
FastEthernet0/1 192.168.1.1 YES manual up up
Serial0/1 12.1.1.1 YES manual up up
APPLY EIGRP ON ALL ROUTERS FOR CONNECTIVITY
R1(config)#router Eigrp 100
R1(config-router)#network 12.1.1.1 0.0.0.255
R1(config)#exit
TUNNEL CONFIGURATION
R1(config)#int tunnel 13
R1(config-if)#ip address 10.3.3.1 255.255.255.0
R1(config-if)#tunnel source s0/1
R1(config-if)#tunnel destination 23.1.1.3
R1#conf t
APPLY RIP FOR TUNNEL CONNECTIVITY
R1(config)#router rip
R1(config-router)#version 2
R1(config-router)#network 192.168.1.0
R1(config-router)#network 10.3.3.0
R1(config-router)#no auto-summary
R1(config-router)#exit
R1#traceroute 192.168.3.3
Type escape sequence to abort.
Tracing the route to 192.168.3.3
1 10.3.3.3 116 msec 112 msec 40 msec
R1# conf t
R1(config)#int tunnel 14
R1(config-if)#ip address 10.4.4.1 255.255.255.0
R1(config-if)#tunnel source s0/1
R1(config-if)#tunnel destination 24.1.1.4
R1#conf t
R1(config)#int tunnel 15
R1(config-if)#ip address 10.5.5.1 255.255.255.0
R1(config-if)#tunnel source s0/1
R1(config-if)#tunnel destination 25.1.1.5
R1(config)#exit
R1#traceroute 10.5.5.5
Type escape sequence to abort.
Tracing the route to 10.5.5.5
1 10.5.5.5 80 msec 84 msec 44 msec
R3(config-if)#int f0/1
R3(config-if)#ip add 192.168.3.3 255.255.255.0
R3(config-if)#no shut
R3(config)#exit
R3#sh ip int br
FastEthernet0/0 23.1.1.3 YES manual up up
FastEthernet0/1 192.168.3.3 YES manual up up
RIP Configuration on R3
R3(config)#router eigrp 100
R3(config-router)#network 23.1.1.3 0.0.0.255
R3(config-router)#
R3(config-router)#exit
R3(config)#int tunnel 13
R3(config-if)#ip address 10.3.3.3 255.255.255.0
R3(config-if)#tunnel source f0/0
R3(config-if)#tunnel destination 12.1.1.1
R3(config-if)#
R3(config)#exit
R3#conf t
R3(config)#router rip
R3(config-router)#version 2
R3(config-router)#network 192.168.3.0
R3(config-router)#network 10.3.3.0
R3(config)#exit
R4#conf t
R4(config)#int f0/0
R4(config-if)#ip add 192.168.4.4 255.255.255.0
R4(config-if)#int f0/1
R4(config-if)#ip add 24.1.1.4 255.255.255.0
R4(config-if)#exit
R4#sh ip int br
FastEthernet0/0 192.168.4.4 YES manual up up
FastEthernet0/1 24.1.1.4 YES manual up up
R4#conf t
R4(config)#router eigrp 100
R4(config-router)#network 24.1.1.4 0.0.0.255
R4(config-router)#exit
R4(config)#int tunnel 14
R4(config-if)#ip address 10.4.4.4
R4(config-if)#ip address 10.4.4.4 255.255.255.0
R4(config-if)#tunnel source f0/1
R4(config-if)#tunnel destination 12.1.1.1
R4(config)#exit
RIP Configuration on R4
R4(config)#router
R4(config-router)#version 2
R4(config-router)#network 192.168.4.4
R4(config-router)#network 10.4.4.0
R5#conf t
R5(config)#int f0/0
R5(config-if)#ip address 192.168.5.5 255.255.255.0
R5(config-if)#no shut
R5(config-if)#exit
R5(config-if)#int f0/1
R5(config-if)#ip address 25.1.1.5 255.255.255.0
R5(config-if)#no shut
R5(config-if)#exit
R5#sh ip int br
FastEthernet0/0 192.168.5.5 YES manual up up
FastEthernet0/1 25.1.1.5 YES manual up up
R5#conf t
R5(config)#router eigrp 100
R5(config-router)#network 25.1.1.5 0.0.0.255
R5(config)#int tunnel 15
R5(config-if)#ip address 10.5.5.5 255.255.255.0
R5(config-if)#tunnel source f0/1
R5(config-if)#tunnel destination 12.1.1.1
R5(config-if)#exit
RIP Configuration on R5
R5(config)#router rip
R5(config-router)#version 2
R5(config-router)#network 192.168.5.5
R5(config-router)#network 10.5.5.0
At the very least, the tunnel source and destination addresses must be specified. Furthermore, the IP subnet must be configured to provide IP connectivity over the tunnel link.
Use the show IP interface command to display GRE tunneling information.
show IP interface.
show IP route.
show IP interface tunnel.
show IP tunnel traffic.
show interface tunnel.
show statistics tunnel.
A Generic Routing Encapsulation tunnel could be used to communicate with a device that is incompatible with your computer. Alternatively, you could use a Generic Routing Encapsulation (GRE) tunnel to ensure that a message reaches its intended recipient despite any protocol issues you suspect exist, even if you are unsure.


![The Best Antivirus Apps For Android - [2023] The Best Antivirus Apps For Android - [2023]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj3Yjm36h1U18dmYifXs9XZCUy6ch_XK0XOXf8hVW4zcVUDW0OiVXQZT0Sr77Yjep1CUOHP3OqlrMIzRJLYasizRmQUilnXjozbQ8D0iroUBbeFEUD2MwaJdGuE4RJaqrfVHFX-_OoIhOyPr_K10ky6goZUJtdqUWIOkCibIoNylnXXzR-AksQYPTQ0/s72-w640-c-h388/antivirus-android-2023.png)
![15 Travel Packing Tips For Holiday: Updated [2023] 15 Travel Packing Tips For Holiday: Updated [2023]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgJfOBYMtma5U34TjVvkOWNnaRwVA_ty2-tKck6tTU24-cAcOu4boybt3T_8BF66hAqzOriHVxJdRbzjLq9ZfhsMAUTQ80ja19GPktAAEnW0WPKQgsKJTXXJzIeKHYE40HeljCSC6UVTJA/s72-w640-c-h360/Travel-packing.jpg)


0 Comments: